Summary
With the advancements in technology, the Cyber World is getting more and more
vulnerable to hacking. One of the ways to attack physical systems is by social
engineering people to insert an infected device into their computers. Modern operating
systems (like Windows, Linux, MAC, etc.) are configured to allow HID-class devices
to communicate with the system without any restrictions. The USB devices that can
be programmed to portray as HID class devices are readily available in the market.
This makes it easy for hackers to build USB devices that portray as HID class devices,
but when inserted into a computer they deploy malware into the system. Even after
knowing the severity of the HID class device attacks, the devices available in the
market still do not have any mechanism to authorize themselves as secure device.
Also, the software solutions to block these unsecure HID devices effectively are not
available in the market.
In this project, I worked on two-fold approach.
First, building secure firmware for HID class devices to provide an authentication
mechanism when connected to a system. And, the second is building computer
software that can authenticate the HID class devices and block the unsecure ones.
Secure HID device Firmware
The firmware designed used the keystroke injection mechanism to authenticate itself. I used the RP2040 based development board with CircuitPython to build the device. The keystrokes for the authentication mechanism can be easily programmed using a text file uploaded to the micro-controller.
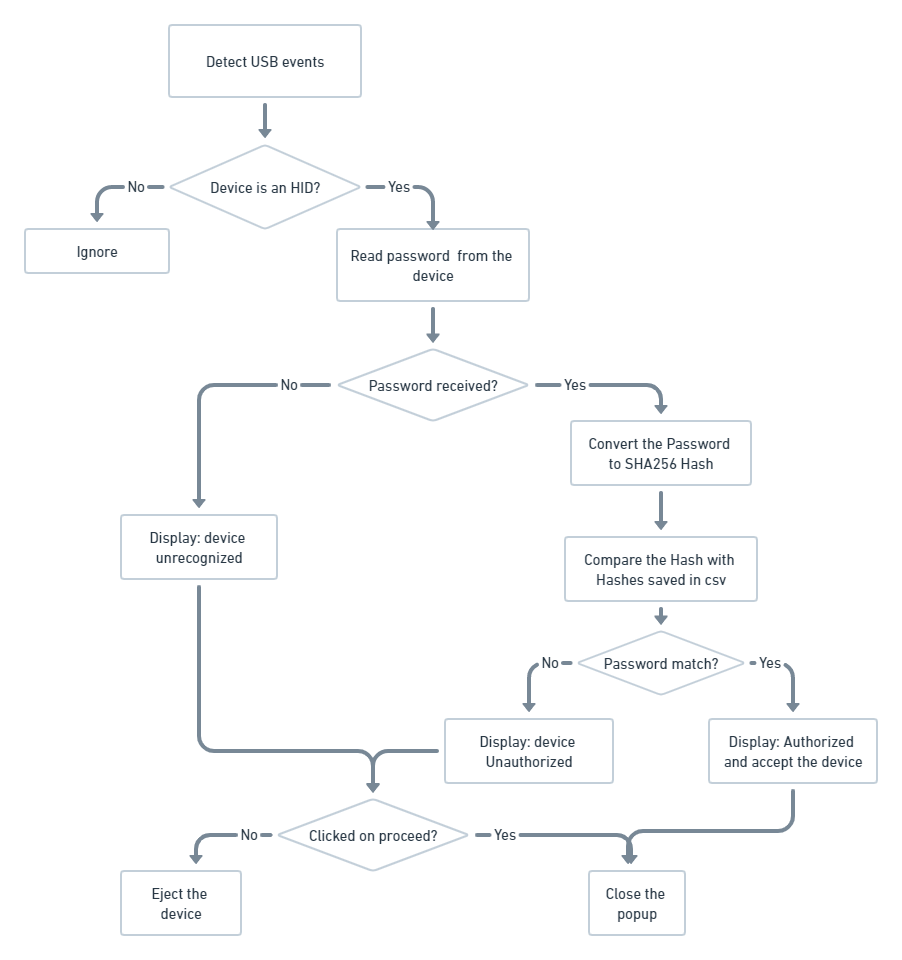
Python Script to authenticate secure device
on the computer end happens through a python script running as a service in background. The script looks for HID device plugged in and matches their VID and PID. Once VID and PID are identified as genuine, it starts reading the keystrokes from the device. The entered keystrokes are then matched with the keys stored in an encrypted file within the computer. Once the keystrokes and stored key match, the device is allowed to work as normal HID device. Otherwise, it is ejected from the device and blocked from future access.